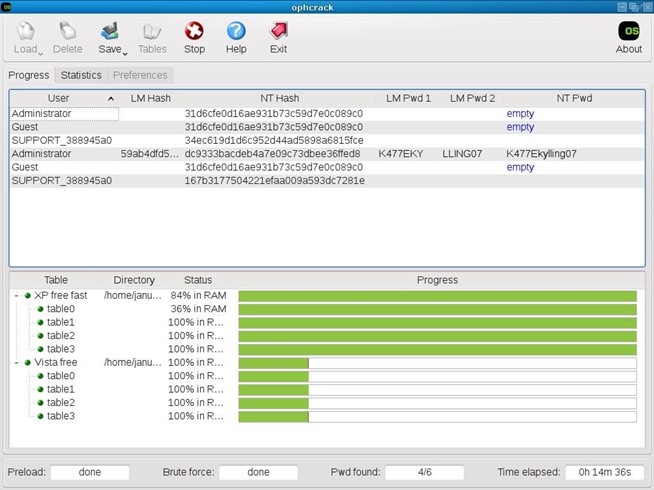
Crack Windows Vista Password Hashed
How are passwords stored in Linux (Understanding hashing with shadow utils)A user account with a corresponding password for that account, is the primary mechanism that can be used for getting access to a Linux machine. Its very much logical to think that the passwords of all the user's in a system must first be saved in some kind of a file or a database, so that it can be verified during a user login attempt. And you do not require the skill set and expertise of a computer security scientist to think rationally that if you get hold of that database or file, which stores all the passwords, you can easily get access to the machine. Some people will argue at this point that the database, or the file that contains the passwords, are in an encoded format (hash value), and its not possible to know the real password, from the encoded password hash. The main strength of the hashing algorithm is the fact that, you cannot detect the original string from the encoded string.
In other words you can call it one way hashing. Avatar Pc Game Activation Keygen Download Pc. You will get a unique fixed length encoded string for any data you give, and that encoded string will be unique to that particular data. In short no two data can have the same hash (encoded string). Changing a single character of the data will produce a completely different encoded hash(Because the data is different). The strength of hashing is used in almost all communication protocol's in some or the other way to check and confirm the originality and integrity of the data(because, if you alter the data the hash will change). But what if an attacker gets hold of the encrypted hash and goes on trying different combination of words to produce the exact same hash. This risk was also applicable to the way passwords were stored in UNIX/Linux system's.
- Cisco type 7 password decrypt hack crack. This page allows users to reveal Cisco Type 7 encrypted passwords. Crack Cisco Secret 5 Passwords. Understand the difference.
- InformationWeek.com: News, analysis and research for business technology professionals, plus peer-to-peer knowledge sharing. Engage with our community.
- How to remove Syskey and Administrator password,How to remove Server 2003 administrator password,How to reset syskey,How to remove window 7 administrator password.
In a Windows network, NT LAN Manager (NTLM) is a suite of Microsoft security protocols that provides authentication, integrity, and confidentiality to users. John the Ripper password cracker. John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS, and OpenVMS. If you would like to read the first part in this article series please go to How I Cracked your Windows Password (Part 1). Introduction. In the first part of this.
Although the passwords were encoded, if an attacker get's hold of that password file, then he can attempt to break the password. From the initial days of Unix, passwords were stored in a file called as /etc/password. Which means any user in the system can read that file. This was done purposely because the file contains critical user related information other than passwords, and many applications and system tools require that information to function properly. Lets see the permission of the /etc/password file in linux. Let's try to change this permission, so that only . Even if you change the user, you will not get the user name, home directory, custom shell etc (Because all these details are stored in /etc/passwd).

Due to this reason the file /etc/passwd, needs to be kept world readable. But we cannot keep passwords in a file that's world readable(because of the risk involved, even though its encoded in a one way hash algorithm)Hence there arises a need to separate passwords from this file and keep it in a file, that's only accessible by root.
The solution to this problem is implemented in the form of a package in Linux called . What is shadow- utils package in Linux? Shadow utils is a package in Linux that's installed by default in most of the distributions, used for separating passwords from /etc/passwd. After implementing shadow- utils, passwords are now saved in /etc/shadow file in Linux. This /etc/shadow file is only accessible by root.
Let's see the contents of the /etc/shadow file, and also its permission. Let's see what's the content of this file. The first field is self explanatory, its the USERNAME2. The second field is the encoded password (Which is a one way hash. The third field is the day's since the UNIX time that password was changed.
Refer: What is UNIX time? This field specifies the number of days, that are required between password changes. No of days after which its necessary to change the password. This is the number of days before the required password change, the user gets a warning. If the password has expired, after this number of days the account will be disabled. No of days from the Unix Time, the account is disabled.
This field is not used yet.. Now you will be confused, that why does the /etc/shadow, file contains these many information's rather than only the encoded password. This is because shadow- util's package provides some more advanced feature's along with storing encoded passwords in /etc/shadow. The above mentioned fields of /etc/shadow, file tell's those added feature's to a certain extent like age of the passwords and its expiry, and also below mentioned feature's. Default parametres for user account creation (/etc/login. Tools to modify user accounts and groups. Enforcing strict password selection.
How is an encoded password stored in /etc/shadow file, and how does the system verify a user typed password during login? For understanding how this entire thing works, let's take the case of the previously shown example entry for root user, from /etc/shadowfile.
Etg. 2Ex. UZ$F9. NTP7omafh. KIlqa. BMqng. 1 The above shown encoded hash value can be further classified into three different fields as below. The first field is a numerical number that tell's you the hashing algorithm that's being used. MD5 hashing algorithm.
The second field is the salt value. Salt value is nothing but a random data that's generated to combine with the original password, inorder to increase the strength of the hash. The last field is the hash value of salt+user password (we will be discussing this shortly). So in our example entry of root, as shown below,$1$Etg. Ex. UZ$F9. NTP7omafh.
KIlqa. BMqng. 1The above shown encoded password is using MD5 hashing algorithm (because the of $1$)Salt value is Etg. Ex. UZ (the content between the second and third $ sign)And the hash value of . Let' s reproduce the same output by providing the salt value of Etg. Ex. UZ and the original password. If that encoded string matches the encoded string from the shadow file, then the user login is considered as successful. Changing the salt will change the entry in shadow file. What will happen if there is no salt value at all?
Salt value is a major component that strengthens the way a linux system stores password. Imagine that there is no salt value applied before storing passwords in linux. As we have discussed in the beginning of this article, a dictionary attack with common dictionary words will become much more easier to do. An attacker cannot easily guess that two user's are using same passwords. Because even if the attacker has somehow gained access to the shadow file, he cannot say looking at two encoded passwords, that they are using the same password. This is because both of them will be having different salt values.
How to Display hashing Algorthm used in your Linux Machine?