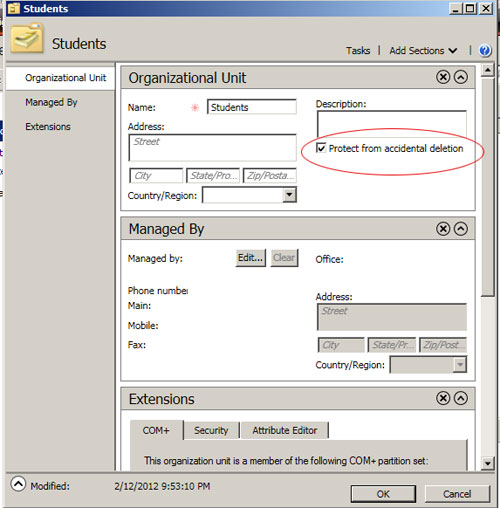
Delete Active Directory Object Protected Accidental Deletion Of Files
Since Microsoft acquired LinkedIn, I’ve been dreading the day notifications to add someone I’ve never met to my professional network pop up in my screen. When Active Directory deletes an object from the directory, it does not physically remove the object from the database. Instead, Active Directory marks the object as.
The folder should have read permission, delete subfolders and files, create folders /append data, create files / write data, read attributes, list folder / read data. IBM Spectrum Scale 6 Proven Steps to the Best Out of Search in SharePoint 2013. Same Active Directory - permissions.
New Features in Version 11. Features and enhancements in this release are listed here, with a link to full documentation for the feature. To see the new features in.
Recovering Active Directory Domain Services. Accidental deletions can occur in any writable directory partition.
Such deletions are most common in the domain directory partition, but they can also occur in the configuration directory partition. Objects in the schema directory partition are protected against deletion. The method for recovering deleted objects is authoritative restore. If you have data loss and you can identify the source and quantity of the loss, you can recover the lost data by performing an authoritative restore. If you lose domain data, you must perform recovery by restoring a domain controller that hosts a writable copy of the domain directory partition where the data loss occurred. If objects are deleted from the configuration directory partition, you can recover these objects by restoring any domain controller in the forest.
There are special considerations if the deleted objects have a forward link- back link relationship with each other. This relationship exists for security groups and distribution groups. Restoring group memberships.
Security principals are objects that can have group memberships. Apc Smart Ups Sc620 Software Store more. Recovering deleted security principals requires not only restoring the object itself but also restoring the group memberships of each restored security principal. You use files that are generated by Ntdsutil during authoritative restore to recover group memberships. Group membership is defined by linked attributes on the group object and on the group member object: the member attribute of the group object is a forward link attribute that links to the member. Of attribute (the back link) of the group member, which can be a user, a computer, or another group.
If you perform the restore on a domain controller that is not a global catalog server, only group memberships for groups that are stored in the domain are restored. If you perform the restore on a global catalog server, group memberships in universal groups that are stored in other domains in the forest are also restored. However, restoring memberships in domain local groups that are stored in other domains requires additional steps that involve using the files that Ntdsutil generates during authoritative restore.
When you authoritatively restore security principals on a domain controller that is running a version of Windows Server later than Windows Server 2. Windows Server 2. Service Pack 1 (SP1), Windows Server 2. Service Pack 2 (SP2), Windows Server 2.
R2, or Windows Server 2. Ntdsutil command- line tool recovers group memberships automatically (restores the member. Of value on the restored security principal object) for all groups that were created or updated at a forest functional level of at least either Windows Server 2. Windows Server 2. However, replication order can undo the restored memberships in the recovery domain. For this reason, it is best to perform the additional steps to recover group memberships in the recovery domain as well.
For more information about restoring group memberships, see Performing Authoritative Restore of Active Directory Objects. Methods of authoritative restore. Depending on replication conditions in the domain of the deletions, you can use the following methods to perform an authoritative restore: Nonauthoritative restore from backup, followed by authoritative restore: Unless you can isolate a domain controller that has not received the deletions, authoritative restore must be preceded by a nonauthoritative restore from backup to restore the directory to a former state that contained the deleted objects. With the deleted objects restored, you can mark them as authoritative so that replication does not overwrite them with the delete condition that still exists on the other domain controllers in the domain. Authoritative restore only: If you identify the data loss quickly and you can isolate a global catalog server in the domain where the deletion occurred that has not received replication of the deletions, you can mark the objects as authoritative on the global catalog server and avoid performing an initial restore from a backup (nonauthoritative restore). This option depends on your ability to stop inbound replication on the global catalog server before replication of the deletions is received.
Global catalog servers often have longer replication latency than other domain controllers. Global catalog servers are preferred as recovery domain controllers because they store more group information. However, any latent domain controller in the domain of the deletions that has not received replication of the deletions can serve as the recovery domain controller if you want to avoid restoring from backup. For more information about performing authoritative restore without restoring from backup, see Performing Authoritative Restore of Active Directory Objects.